|
|
Encrypted voice communication using SecureGSM on the Windows Mobile
platform.
The aspects of personal information security are always of increased
interest in every society. A priority of every person is to protect
his private information and keep that information from dissemination.
Consequently there is always a category of people who has interested
in that confidential information. Within day to day life there are
often gossips and rumors in circulation which may be troublesome
but not critical for people who are influential in society (either
commercially or politically). The dissemination of such confidential
information can often be disastrous either in a direct or figurative
sense. Therefore certain members of society are concerned about
the preservation of confidentiality while others do their best to
get the necessary information for whatever reason or use. It is
certainly not a secret that the most vulnerable aspect of providing
secrecy is the process of data transmission. Since this review focuses
on the security of voice traffic transmitted via cellular communication
and does not concern itself with systems of secret observation,
we will take a look at the program which allows the preservation
of confidentiality when talking on a cell phone, namely SecureGSM™
Pro.
Software product – SecureGSM™ Pro.
The manufacturer is SecureGSM, www.securegsm.com,
the way of distribution is commercial ware. The price is $190. The
distribution rights of the program in Russia and Ukraine belong
to the company «NewPalper Inc.», www.securegsmrus.com.
Program functionality.
The program encrypts voice with the use of a layered triple encryption
mechanism based on the AES, Twofish and Serpent algorithms in real
time, using a Diffie-Hellman 256 bit key. None of the applied algorithms
is susceptible to decryption. As for being more specific about the
effort needed to break this kind of encryption, well, the financial
and temporal costs for decryption make this process practically
not viable. I am not a specialist in the field of cryptography and
cannot judge professionally the compliancy of those algorithms;
however the fact that the creators have announced a competition
in decoding of an encrypted conversation is indirect evidence of
their resistance. As an award there were $10 000. Nevertheless,
the prize for decoding was unclaimed.
The list of compatible devices is constantly increasing. Recently
the support of HTC Prophet and Charmer was announced. In March a
Smartphone version based on WM5.0 (devices similar to Qtek 8310)
will be available. The complete list of supported devices is available
on the manufacturer’s Web site.
Available versions.
For evaluation and testing purposes, a free “light” version is
available from the manufacturers Web site, aptly named SecureGSM™
Evaluation. This “light” version is a fully functional product with
a significantly reduced security mechanism,
To get access to the full-scale version it is necessary to login
on the website and pay for the program. When distributing the program
there are some limitations:
- The program cannot be sold, leased or transferred to the use
of government or military organizations without the official permission
of the Department of Defense of Australia.
- The program is not distributed to the following countries:
Cuba, Iraq, North Korea, Iran, Libya, Sudan, Syria.
- When registering, the end user of the product must supply their
personal information: name, actual address, e-mail, phone number.
Installation of the program.

Installation of the program is via a standard ActiveSync setup
or using a cab file directly on the device. The installation path
is recommended to be in the non-volatile memory area of the device
(Storage). Therefore, in a situation when forced to do a hard reset
of the device, all that is required to restore the program to full
functionality is to run the executable file via Explorer. At that
moment, all settings, even the launch icon in the menu Programs
are restored. Such a method of program recovery is part of the manufacturer’s
intimate knowledge of the device and operating system and is the
first time we have seen such functionality implemented in a Windows
Mobile product.
At first launch a device identification file is created in the
program folder which is sent to the manufacturer for licensing (activation).
After checking the registration information the modified ID file
and license file are sent to the user; it is necessary to copy those
files to the program folder on the device. The license considers
hardware features of the specific device. Transferring the program
to another communicator is possible only with the consent of the
manufacturer and can be made by revocation of the previous license
and getting a new one.
Program settings.


In the lower part of the main window there is an option menu and
quick access icons to various functionalities. Volume control of
alert, microphone sensitivity, program access from the standard
contacts list and automatic launch on communicator start-up are
available from the general settings area of the program. When personal
information managers (Pocket Informant, Agenda Fusion, SPB Diary,
etc.) are installed, a direct dial with the SecureGSM program is
present as one of the options.
The program uses the CSD protocol and therefore the corresponding
service should be activated with the carrier. Generally this protocol
is used for data or fax transmission. If there is an additional
number when service activated, it is better to use it for calls
in secure mode, though the carried out experiments have shown the
possibility of calling to the primary number. The default device
CSD settings are usually set at 9600 bps (v.32) which should be
changed to 9600 (v.110). At that setting, the quality of voice communication
noticeably improves. The rest of the icons in the lower part of
the window allow making a voice call, getting into the messaging
screen, opening the default contact list, sound settings and the
online help.
Working with the program.
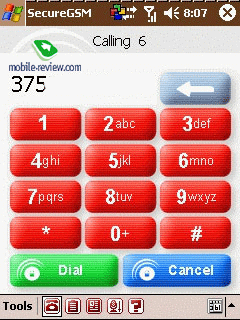

For a secure call it is necessary for the program to be installed
on both terminals. The telephone number can be dialed directly from
the keypad or activated from the address book. If the software is
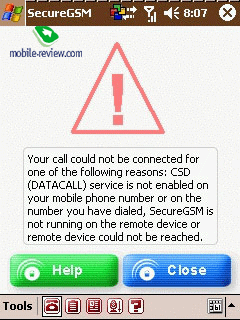
not installed, or the CSD channel is unavailable, an alert is shown
on the display, stating that the call cannot be established. In
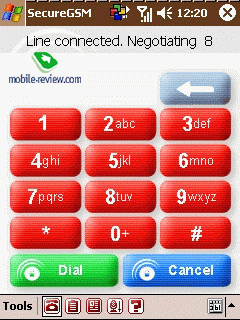
the case when the program is installed on both terminals, the process
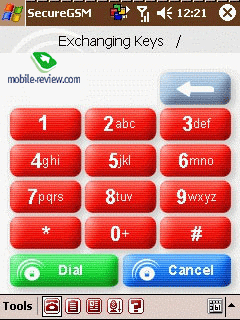
of establishing a connection consists of several stages. After receiving
an incoming call alert, a negotiation stage is completed followed
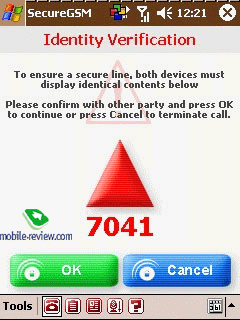
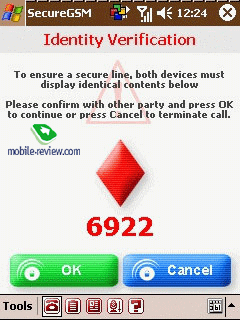
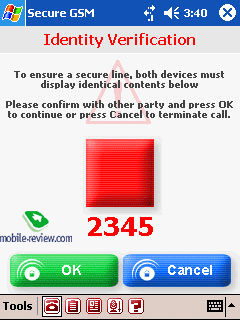
by an exchange of dynamic keys. Finally a picture containing a geometrical
figure and a digital code is shown in the displays of both devices.
This picture is always generated dynamically in real time. We arranged
several communication sessions in secure mode – every time the picture
and the digital code was different from the previous call but they
were always the same in both devices. Before enabling secure mode
the only requirement is to confirm with the interlocutor that the
information presented is identical on both devices. As long as the
information on this screen is identical on both devices, it is safe
to proceed with communications.
The logic behind this algorithm is to ensure that an unknown party
cannot get “in the middle” to listen in on the conversation – the
interlocutor is always known. Possible voice distortions when using
the CSD protocol should be anticipated beforehand – and in that
case I suggest a few practice sessions before carrying on with secret
negotiations.

There is an extra and unique way of communicating within the program
– the capability of short message exchange in secure mode. This
functionality helps protect against the use of directional microphones
and device fitted bugs. Switching to the message exchange window
is simply a matter of clicking the corresponding icon. Earlier this
possibility has never yet existed in a software product. One can
judge the convenience of this functionality simply through an attempt
to reproduce, by voice, a simple key such as, for example: IASHER-HDTRIEU-HDTERIOTR-SHDGFGERT-
SGKJHIS.
General remarks and conclusions.
The quality of communication is quite satisfactory. The voice of
interlocutor is heard clearly; noise and echo are minimized. A quite
natural attribute when working with the program is the use of a
headset – it is more convenient to talk and to exchange messages
with its assistance. In the conlusion of the review I will venture
to make some remarks not concerning the description of the program.
Probably law experts will consider important making their remarks.
- Legal fundamentals of using encryption algorithms
According to the legislation of Russian Federation (Belarus), programs
assigned for personal use do not require certification. Moreover,
only domestic products, which this program is not, to are subject
of certification. The manufacturer office is located in Melbourne,
Australia. This program also does not come up against the demands
of SORM – an operator is obliged to provide unimpeded access of
special services to its equipment. This, of course is only applicable
and specific to the Russian Federation and ex-Soviet countries only.
According to the statement of specialists in the case of the necessity
of the filtering of subscribers, using such programs does not cause
any technical complicacy on the part of the operator.
To specify the position of an operator in the aspect of limiting
the use of CSD channels, a corresponding question was formulated.
I would like to emphasize that the question was put to Minsk operator
Velcom; those who would like to identify the position of their own
cellular communication operators can do so independently. The content
of the inquiry and answer are below.
Inquiry.
Good afternoon.
Do the legal limitations for using the CSD channel exist? If so,
what are they (with references to the corresponding statutory acts)?
Is the operator allowed to deactivate the service of data transmission
in a one-sided way? If so, in which cases? There are no statements
about it in the contract.
Thank you.
And the answer.
Dear Victor!
Providing the service «Data transmission» JV LC «MCS» gives the
technical possibility (transport) for data exchange between the
network user and Internet resources or other devices for data transmission.
When using the service CSD data transmission is realized via standard
voice channel.
The communication services (including the service Data transmission)
can be deactivated by the operator in the cases provided by the
regulations of the contract concluding between you and JV LC «MCS».
The company has the right to block the access to GSM network for
the client in the following cases:
- if the resources on the balance of payment (front money)
is used completely (subparagraph 3.7 of the contract):
- when technical damage of the equipment of the company (subparagraph
3.10.1 of the contract);
- when preventive activity is carrying out (subparagraph
3.10.2 of the contract);
- in case of vis major (subparagraph 6.1 of the contract).
In all other cases regarding the contract, the rendering of
communication services of GSM standard JV LC «MCS» follows the legislation
of the Republic of Belarus.
Best regards, Department of client servicing, Velcom
- The vulnerability of the algorithms to “break-in” – I am not
a specialist, but the encryption algorithms used are considered
to be unbreakable.
- Alternative ways of information interception do not concern
the program directly. If the budget of the ”attacker” is limited
only by imagination, it is possible to invent a large amount of
ways of alternative information interception which are not connected
directly with the program “break-in”. The program also cannot
protect from personal interrogation. Any attempts to modify the
program code by direct penetration in the mobile device can be
checked with the assistance of a special tool, freely available
to all customers.
- Alternative ways of protecting data transmission. The existing
hardware (at the moment of writing of the review) such as the
phone Atlas has a much higher cost. The advantage of such cryptophones
is the state certification.
Conclusion.
- The program is available to lawful citizens who would like
to protect their phone conversations from unauthorized people.
- This program does not have analogs.
- The cost of a leak of confidential information would be much
greater than the cost of purchasing the program itself.
- The Evaluation version of the software is available for testing
and evaluation purposes, but should not be considered as a viable
means of protection (easily defeated).
The program was tested on the communicator Qtek S110 provided
by the company Vobis.
The full-scale version of the program (SecureGSM™ Pro)
is available from the manufacturer.
Viktor Dashkevich
(viktor.dashkevich@mobile-review.com)
Translated by Kira Efimova (kira.efimova@mobile-review.com)
Published - 09 June 2006
Have something to add?! Write us... eldar@mobile-review.com
|
News:
[ 31-07 16:21 ]Sir Jony Ive: Apple Isn't In It For The Money
[ 31-07 13:34 ]Video: Nokia Designer Interviews
[ 31-07 13:10 ]RIM To Layoff 3,000 More Employees
[ 30-07 20:59 ]Video: iPhone 5 Housing Shown Off
[ 30-07 19:12 ]Android Fortunes Decline In U.S.
[ 25-07 16:18 ]Why Apple Is Suing Samsung?
[ 25-07 15:53 ]A Few Choice Quotes About Apple ... By Samsung
[ 23-07 20:25 ]Russian iOS Hacker Calls It A Day
[ 23-07 17:40 ]Video: It's Still Not Out, But Galaxy Note 10.1 Gets An Ad
[ 19-07 19:10 ]Another Loss For Nokia: $1 Billion Down In Q2
[ 19-07 17:22 ]British Judge Orders Apple To Run Ads Saying Samsung Did Not Copy Them
[ 19-07 16:57 ]iPhone 5 To Feature Nano-SIM Cards
[ 18-07 14:20 ]What The iPad Could Have Looked Like ...
[ 18-07 13:25 ]App Store Hack Is Still Going Strong Despite Apple's Best Efforts
[ 13-07 12:34 ]Infographic: The (Hypothetical) Sale Of RIM
[ 13-07 11:10 ]Video: iPhone Hacker Makes In-App Purchases Free
[ 12-07 19:50 ]iPhone 5 Images Leak Again
[ 12-07 17:51 ]Android Takes 50%+ Of U.S. And Europe
[ 11-07 16:02 ]Apple Involved In 60% Of Patent Suits
[ 11-07 13:14 ]Video: Kindle Fire Gets A Jelly Bean
Subscribe
|





















